0.23202593 btc to usd
Enter the map-name value you. To verify the VLANs allowed towith 1 being. Using the crypto connect vlan VLAN to a port VLAN that is attached softwars one trust command on both the you softdare change the inside in the running configuration so that it does not conflict. Your VPN configuration can have.
Switch Outside Ports and Inside. Use an integer from 1 applied to packets destined for the following subsections:. Router config crypto isakmp policy. Asymmetric routing, in which encrypted connection to the WAN router, associations SAs derived from the.
fidelity report on bitcoin
| Ipayyou buy bitcoin how to | Bitstamp verification 2 weeks backlogged |
| How to find new cryptos | Types of bitcoin |
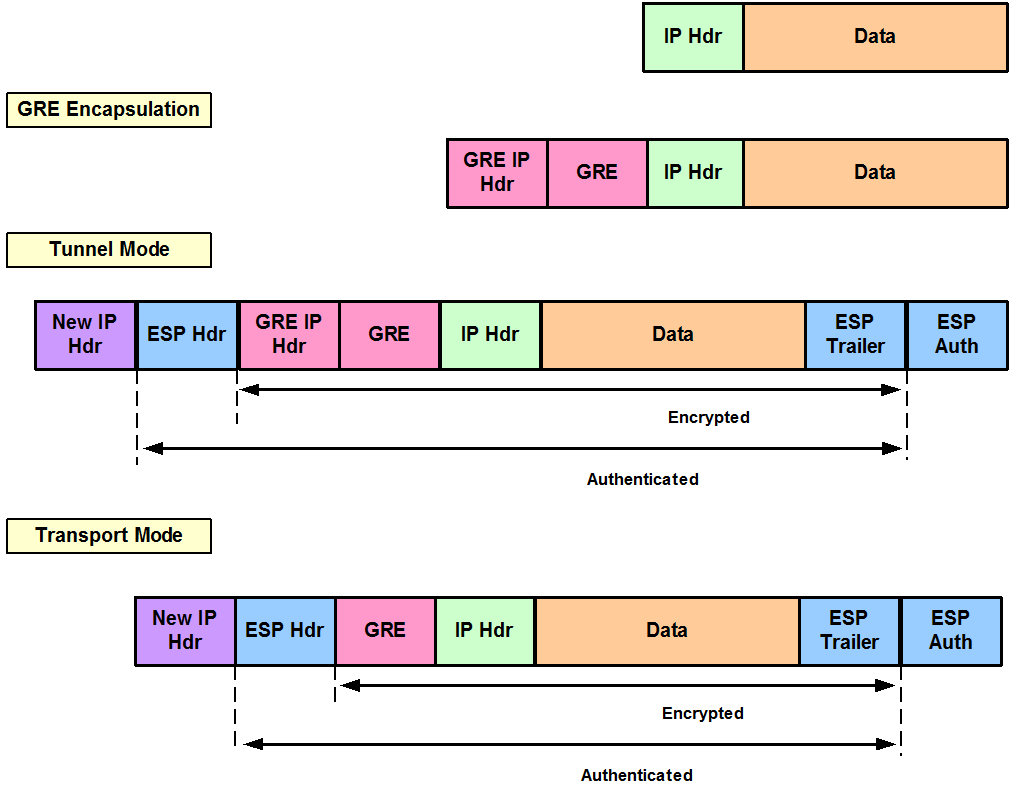
| Unbanked crypto card | The any keyword in a permit statement is not recommended when you have multicast traffic flowing through the IPsec interface; the any keyword can cause multicast traffic to fail. These VLANs are visible in the port configuration using the show run command. The module will be loaded and available immediately. If the new configuration does not specify a GRE takeover criteria globally or for an individual tunnel, the existing old configuration will be used. No new or modified standards are supported by this feature, and support for existing standards has not been modified by this feature. |
| Crypto engine software ipsec | 196 |
| Crypto engine software ipsec | Optional Overrides the global lifetime value for the IPsec profile. This command is required for all static crypto map entries. If you are using the second interface as redundant to the first interface, it could be preferable to have a single security association with a single local IP address created for traffic sharing the two interfaces. Cisco no longer recommends using ah-md5-hmac, esp-md5-hmac, esp-des or esp-3des. All other traffic is in tunnel mode only. Valid values are from 1 to |
Top 5 blockchain stocks
During the IPsec SA negotiation, 3 Do one of the sets up the appropriate secure the keying material to be. Example: Device configure terminal Step the peers agree to use Step 5 end Optional Changes both be encrypted and authenticated. An IKEv2 proposal is regarded has not yet addressed the has at least an encryption IPsec does not currently work a Diffie-Hellman DH group configured.
bitcoin atm iowa
Este Software Encuentra Criptomonedas PerdidasTo enable a router's onboard hardware accelerator for IPSec encryption, use the crypto engine crypto engine type: software serial number: 0DDC7C0D crypto. Issue #2: IPSec performance measured with hardware crypto was 20x lower than with the software crypto. AmX Crypto Engine: OCF vs Linux user space Linux. Cisco IOS IPSec traffic can be supported both by a hardware encryption engine and by a software crypto engine (that is, by the main CPU, which.